
Securing Industrial Control Systems (ICS) and Supervisory Control and Data Acquisition (SCADA) systems is a program management effort. To be successful it is a process that must be institutionalized, and it has to be part of the organizational culture.
CommTech Systems as a member of the International Society of Automation, follows ICS Cybersecurity process as outlined in the International Society for Automation / International Electrotechnical Commission (ISA/IEC) standard 62443, and the National Institute of Standards and Technology, Special Publication (NIST SP) 800-82 Guide to Industrial Control Systems (ICS) Cybersecurity. What is common in these standards is an all hazards approach to system risk, and the need for a process that that encompasses strategies for risk identification, training, monitoring, system testing, and a feedback process focused on system security improvement.
Much of what these standards require are policy and procedures that are designed to secure the system and resilience. Resilience is in terms of a continuity of operations, recovery, and a means to continually improve security.
In addition to the ISA/IEC and NIST standards there are also a host of industry specific standards some of these are listed below:
Reasons why ICS Cybersecurity is not the same as IT (Information Technology) Cybersecurity

Both IT and ICS cybersecurity address the safety and security of their respective environments by using many of the same tools and procedures.
However, the focus is different. In terms of ICS systems, the primary focus of effort is safety; this is in terms of personnel and environmental safety. For most IT systems, this is not a consideration.
Next is the architecture, the ICS focus is on the controllers that make up the ICS system. In terms of IT systems, the focus is on the system server, the network, and the devices on the network. Another difference is the disparate nature of ICS systems, ICS systems almost by definition contain controllers that are old, dissimilar, special purpose, and are a collection of products from different manufacturers. This means that ICS systems are much more complicated, in that they are not standardized, and to replace them requires considerable cost, risk, and time.
Another element is that that ICS systems are real-time. Most ICS systems cannot be shut down, and system down time is not acceptable. In many instances ICS systems are services as in utilities, or production systems that cannot be shut down with extensive disruption, or cost. This requires extensive prior planning and backup systems. For IT systems, system down time is routine and acceptable as it is the nature of the system.
The Process
The question is often where to begin and how.
The process of developing a industrial control cybersecurity system can be outlined in the following cybersecurity standards: the ISA-99 (International Society for Automation, Industrial Automation and Control System (IACS) Security), NIST SP 800-82 (National Institute of Standards and Technology, Special Publication, Guide to Industrial Control Systems (ICS) Security); and the IEC-62443 (International Electrotechnical Commission (IEC), ICS security standards, the equivalent to ISA-99).
A foundation element is the concept of defense in depth
Defense in depth is the concept that includes physical security, personnel security and the elements of Cybersecurity. The goal of defense in depth is to erect barriers to unauthorized entry, it goes the heart of deter, detect, deny, delay and defend Some of these elements are included in the diagram focused on defense in depth.
Defense in Depth

The ISA diagram has three major sections it is important to note that these sections need to be addressed in their sequence order. In general, the first section establishes the business process and the requirements, which in this context are the risks. The second section is focused on the development of the Cyber-Security Management System (CSMS). The third section is the enduring tasks of monitoring and improving the CSMS.
All of the standards mentioned above, as well as the industry specific standards begin with a description of the system and its business rational or its framework for existing. The first section is focused on the risk assessment based on the business framework. The point is that risks are dependent on the nature of the business enterprise, and the risks are driven by the degree of acceptable risk, or risk appetite; and the types of services or the type of production.
In the second section, the risks are addressed by developing the CSMS system which will provide the foundation in terms of the ICS Cybersecurity infrastructure. There are essentially three pillars of effort in this section. First is developing a security policy, organization and awareness, here the focus is on defining the CSMS scope, training and awareness, and developing security policies and procedures. Second is focused-on security counter measures. Here the focus is on personnel, physical and environmental security, network segmentation and access control. The third pillar is risk management, CSMS maintenance, documentation, and incident response planning.
The third section is devoted to sustainment, no system can exist without adjustment to the threats in its environment. The point here is improvement through continuous feedback. There is no relief to the attacks on the system. As these attacks continue and change due to the defense, the defense too must change to meet these new threats. The third section is the effort devoted to maintaining the system, continuously monitoring and upgrading the CSMS systems defense against new and emerging threats.
.
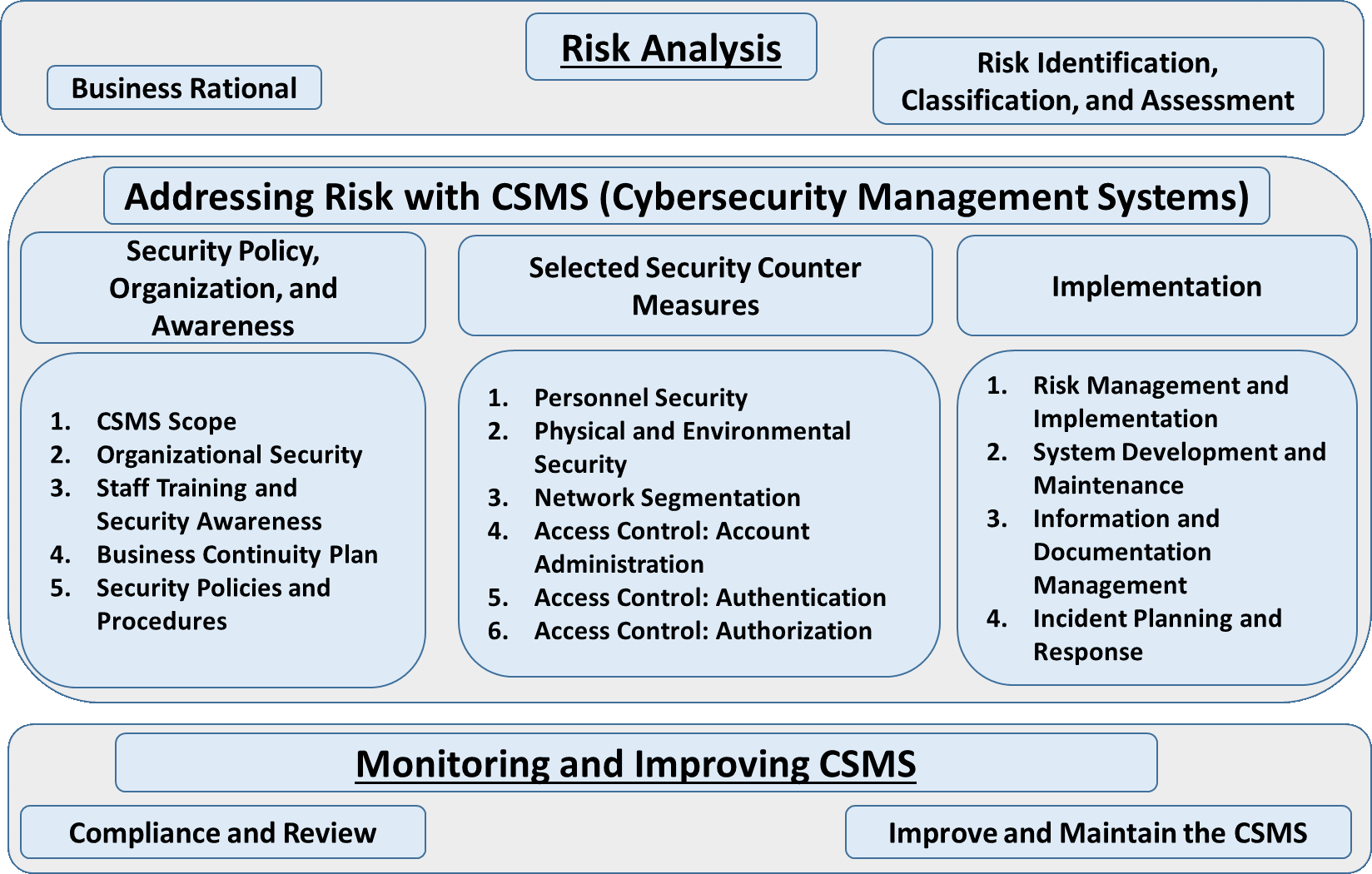
(The system diagram is the International Society for Automation / International Electrotechnical Commission (ISA/IEC) standard 62443, this is the process for instituting and maintaining an Industrial Control System, CyberSecurity Management System (CSMS).)
What we do
We provide technical services that help build, establish, and audit ICS Cybersecurity Systems. We take a project management approach to establishing ICS Cybersecurity programs. The CommTech Systems staff consists of professionals that have worked in both the military and in the Department of Homeland Security (DHS). We have experience in developing plans that protect critical infrastructure, as part of the national Critical Infrastructure Protection (CIP) effort as directed by DHS. Our staff has certified professional project managers, by the PMI. In addition to experience in working with and implementing the standards mentioned above in ICS and SCADA systems.
Our customers include the US Navy SPAWAR (Space and Naval Warfare Command) Pacific, and DHS (Department of Homeland Security).
CommTech Systems Inc. is a California State Certified Small Business DVBE (Disabled Veteran Business Enterprise DGS No. 41194) as well as being a Certified SDVOSB (Service Disabled Veteran Owned Small Business). See NAICS and PCS codes
